We all might have looked and some of us have created many apps as well as websites but have you ever focused on the security of that software?
Is your software safe from hackers attacking it? If not, what security features should a software contain?
What is security?
The protection of computer systems and information from harm, theft, and unauthorized use refers to computer security. i.e. Preventive measures taken to prevent hacking.
Features:
🔸Confidentiality
🔸Integrity
🔸Authentication
🔸Non-repudiation
Confidentiality
Confidentiality refers to that only authorized persons can access the data and no one else can. This can be achieved through encryption and decryption.
The sender can encrypt the message and send it across the channel and the receiver can decrypt the message and read the data. A man in the middle can't understand the data because he doesn't have the key to decrypt the message.
Hence confidentiality is achieved.
Integrity
Integrity refers to that only authorized persons can modify the data and no one else can. This can be achieved through the hash. The hash of every message is unique and is changed even if a small change in the message occurs.
The sender can encrypt the hash and send it across the channel and the receiver can calculate the hash of the message again and check whether the message was changed or not.
If the message is changed, the hash also changes, and hence receiver comes to know whether the message has tampered on the channel or not. Hence, integrity is achieved.
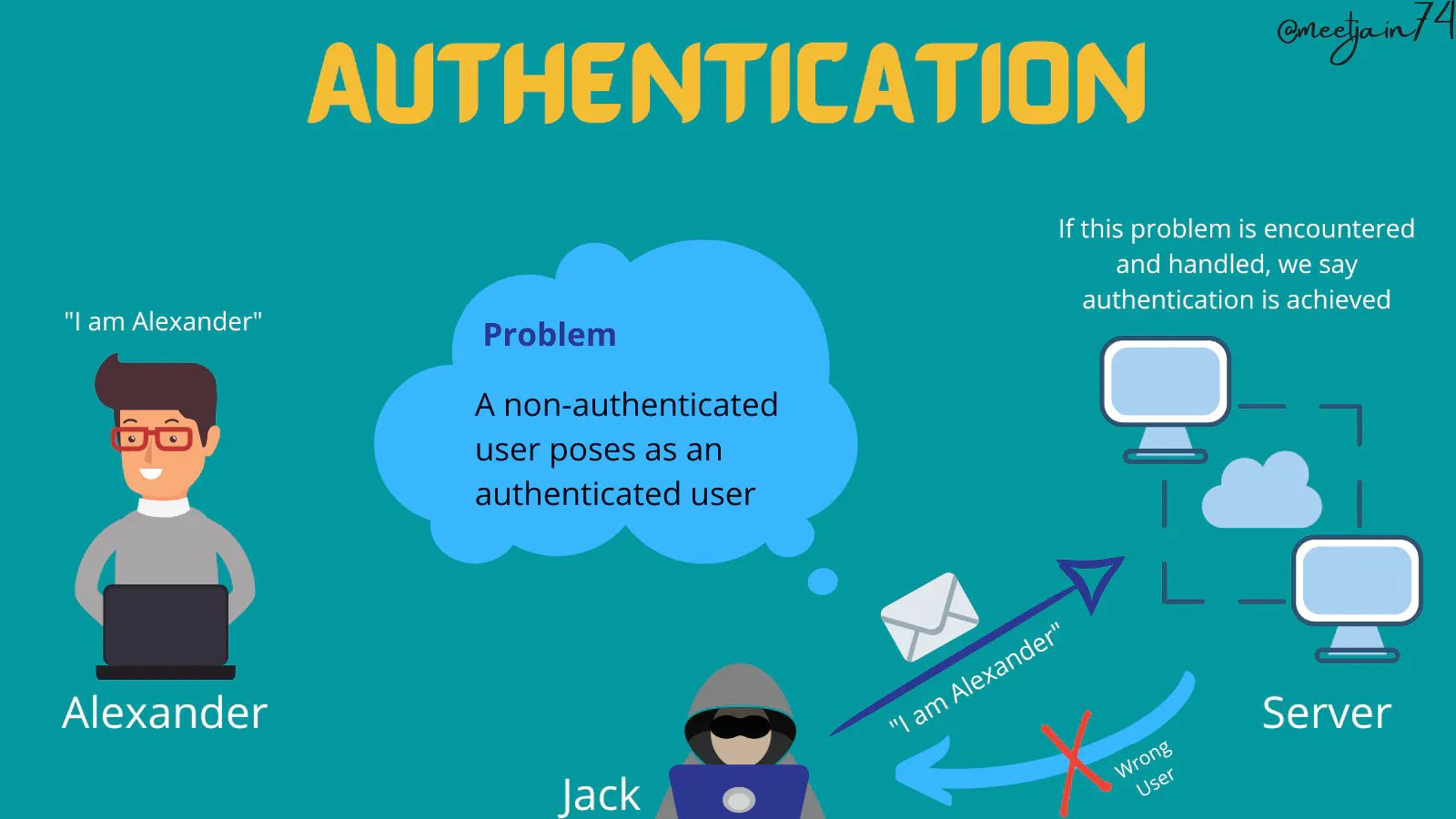
Authentication
Authentication refers to verifying that users are who they say they are and that each input arriving at the system came from a trusted source. This can be achieved through public-key encryption as well as using message authentication code(MAC)
Non-repudiation
Non-repudiation refers to the fact that if a sender sends a message to the receiver then the sender can't disagree with the fact that he/she sent the message to the receiver. It can be achieved with the use of digital signatures.
Depending on the security parameters an organization requires, the appropriate steps are followed to achieve these security features. Example: Posts in Google Classroom do not require confidentiality as if anyone reads the announcement, it doesn't lead to any failure.
Hence depending on your application, follow perfect secure design guidelines and try to make your system secure.
Conclusion
This is the end of the blog. I think you understand how security should be thought of while designing a system.
I hope you find it helpful. Let me know your thoughts in the comments below.
Do like this blog and follow me!
Also, you could follow me on Twitter
Thanks for reading💛